 "...And Jack Left Town" is designed to be a post-introductory adventure for
Cybergeneration: Revolution by R. Talsorian Games. Introductory characters or Experienced
characters can be used, but the difficulty of encounters will need to adjusted upwards as
necessary to make this story a survivable challenge.
"...And Jack Left Town" is designed to be a post-introductory adventure for
Cybergeneration: Revolution by R. Talsorian Games. Introductory characters or Experienced
characters can be used, but the difficulty of encounters will need to adjusted upwards as
necessary to make this story a survivable challenge.
The Story Synopsis (part one):
Rache approaches the group with a mission that they shouldn't refuse. They must plan and perform a raid on a fledgling software company to get a piece of software. The physical and net-based assaults on the office need to come off together to prevent CorpSec from coming down on the group's collective heads. Still, when they do finally get the data from the Corp office, the world starts to crash down around them as various groups try to get the info from them.
A Quick History Lesson for the GM:
Turn to page 210 of the rulebook right now, and read the entire section on Rache. He's an crazy frakin hacker, but he's also the best there is. Two days ago, Rache was just fishing in one of YYY's data files when a nasty piece of black ICE started chasing him around the system. On his way out, the Ghostlord caught a glimpse of a message from a VP at YYY about the T112 test program (see sidebar). The message was terribly informative, but give Rache little more than a desire to crush the project like a bug. There was no doubt that info about T112 "needed to be free", but Rache also realized that T112 couldn't be accessed from the net. As part of their computer internal security, the most secure programs could only be read or accessed from within the company compound. Rache has decided to send in a team to recover the files for him which he will then upload for a live satellite broadcast. Big Fun.
YYY has been working on Project T112 with AIM Overwatch for about 2 years, and is planning to turn over the software (for a hefty fee) very soon. YYY's software has been thoroughly tested on subjects that AIM Overwatch provided. T112 has perfomed marvelously in the trial runs and is such a simple and compact program that it is nearly invisible to the Wizards that run around the system (treared as stealth, FCT 8).
YYY and AIM Overwarch obviously would not like to have this knowlelge become public record. Even in these paranoid and uncertain times, the callous and indescriminate executions of T112 would be considered bad public relations. Rache has other ideas.
Unbeknownst to Rache or the players, the group has been tailed and observed for the last two months by operatives of Arasaka Corp using long Range scopes and mikes, as well as simply having operatives walking by at opportune moments, Arasaka has determined that the group is indeed made up of cyber evolved children, and has targeted them for abduction in the very near future. They are simply waiting for the heat from another group to turn up, so that they will look like saviors as they "rescue" the team.
The Set-Up
On a crummy Saturday morning (like many other crummy Saturdays), a package arrives at the group's headquarters/domicile/whatever. It is addressed to the character with the highest REF (especially a wizard). There is no return address, except for the name "Ghostlord". Inside is a V Smartcard, with no markings of any kind. When one of the group decides to play it, contained on the card, they see the following: whisps of smoke drift slowly up from the floor and form into the ghostly image of a man. He has no distinguishing features and is of normal height/weight/etc. After about 10 seconds, the image speaks.
"Hey pukes. You 'know me. I'm Rache. I know you. You're dogmeat. But right now, you're dogmeat that I need, so, pay attention and you might even earn some lunch money. I got a tiny little glimpse of message of a datafile that you and I both want. You, my little darlings, are gonna get it for us. YYY has been using some poor sap wizards as guinea pigs and they've come up with something that's so frackin nasty that even the Gireat Ghostlord is trying to decide whether or not to sweat..What it is? Glad you asked. It's bad-ass puppy dog. A Bloodhound that tracks you wannabe Raches around the network. It can follow a Wizard around the system and call enough thunder down on his backside that he'll never sit down again. Now, I wouldn't mind seeing fewer snots around the net, but that would make Alt unhappy, so, I'm gonna let you do something about it.
LISTEN UP! You've got to get inside of YYY's office and jack this card (yes, the same one you're listening to right now, weefboy) into their system. There's a little beautey I wrote to grab the file we want and then drop The Wrath of Rache on their system. Snap, Crackle, Pop! Once that's done, all you have to do is bring the pretty card to some friends of mine at the Rock & Taco in the Uptown Mall, and I'll be done with you.
"Now, Here's the location of the office that's got the file. It seems that they don't trust little ol' me, because you can't access the file from an external line. They've got a self-contained system on-site to handle their most sensitive material, so you're going to have to get into the offices and get your hands on the file manually. That's right, I said 'Manually'. That's by hand. That means work. Here's the message I saw.
Have the characters make a computers roll at a 10 (schoolin' at a 15 or an INT at 20). Depending on how well they roll, give them a certain amount of information about T112. One part that they should definitely get is that YYY will be completing the deal with AIM Overwatch to give over this software on Monday to allow AIM Overwatch to distribute it to the various branches of the ISA.
"You'll have to find the office of this Dr. Kisada. It should be pretty simple even for little snots like yourselves. So, all together now: Number 1: get in the office. Number 2: jack the card to copy the files - and 'Rache' the system. Number 3: delete the backups. Number 4: Do what you do best -- Run like hell. Got it? Good. Any questions? [Pause until the players say something]
What's that? Speak up ya half pint! I said speak up! [Pause again]
Oh, yeah. I'm a recording! Ah hahahahaha! You brats are gonna have to wise up if you're gonna survive this. There's a Chrystar Nova parked outside -- I've hacked it with some fake codes that should fool it into working for you and get you out and back." (The Nova is stock except that it will follow the group's commands for the next 48 hours.)
If the group does not contain an netrunner or Wizard, then Rache will have to take responsibiliry himself for the cyberspace aspect of the operarion. Read the following "I'll be running around inside of YYY's system trying to break down their security as much as possible. But I promise you Jack. Give me a call at 555-1234 an hour before you're going to do the run."
If Rache does end up performing the run (or even if the group has a wizard to do it -- Rache is so full of himself), he will be able to shut down any of the security systems whenever he needs. He will let the heat tum up on the group, but never get too hot -- he wants to see what this group is made of and is trying to figure out if he wants to use them again in the figure.
At this point, the figure begins to dissipate and Rache again gets in the last word: "Oh yeah, fill in the name of the character that the package was addressed to. I hope you still have that account that Morgan set up for you so long ago -- I've dumped $2,000 into it for this run, but EVERYTHING [this part is almost painfully loud] has to get incinerated afterwards. Burn your clothes. Fry a computer if you use it. If you touch something between now and monday night, it had better be smoking frackin rubble on Tuesday or your smelly asses are mine. No trails, got it?" The whisps of smoke hnally disappear and the Vsim shuts off.
What's next is up to your players. They've got until Monday morning to pull this thing off or T112 will go from theory to reality.
T112
T112 is the codename of the program that was has developed with AIM Overwatch in order to "reduce rhe spread of the Carbon Plague". Almost two years ago, a netrunner on YYY's staff noticed the work of a group of Wizards for the first time. Intrigued by the near-limitless possibilities, she tried to follow some of these wizards around to learn more about them. Mostly, the wizards were wary of her and avoided her, but on occasion their egos caught up with them, and their private "audience" was given a show of power.
After about six months of this, her hobby evolved into a possible commercial venture. YYY was still a fledgling software company, but when their houshot 'mnner came to them with a plan to track the elusive wizards, they knew they had something. The bright and enterprising young hacker hasn't been seen around the halls of YYY since then, and whether she has moved on to bigger and better projects, is running this project secretly, or if she has simply been "removed from consideration" is unknown.
What YYY has developed is a piece of software that can detect and track traces of a Wizard's movements within a system. Because of the unusual way that Wizards interact with the system, they leave a slightly different kind of trail behind them than does a typical netrunner. There are only about three people within YYY and one or two more outside YYY that are aware of these traces -- most of the people working on the project just know that they are supposed to be able to follow a certain type of track.
The intended use for T112 is that if it is linked to a Anti-Personnel program, it can be sent tO roaming around a companies system looking for any Wizard that happens to be wandering around, and fry 'em without ever bothering standard netrunners (either intemal or external). The more insidious use for it that ISA has considered is that this same pairing could be released out into the net and Wizards would never be safe in Netspace again.
Preparations:
 Here ue some things that the team can look
into before they go charging blindly into the
office compound:
Here ue some things that the team can look
into before they go charging blindly into the
office compound:
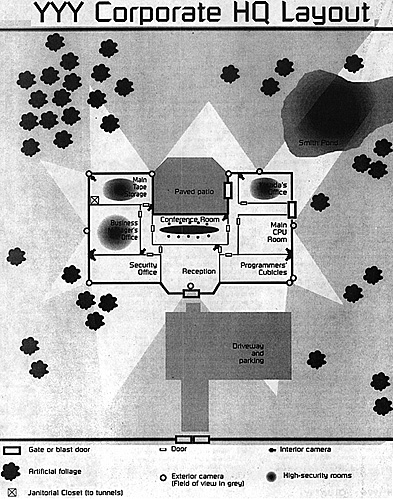
There are floor plans of the offices available in the city planner's office, but it's closed until Monday. They could try to hack into the system to try to get the plans, and it shouldn't be very tough at all considering that the files are mostly public accessible.
Doing surveillance on the exterior of the complex will give them a summary of the exterior security including guard movements, obvious sensors, etc. A wizard/runner may wish to do an exploratory run against the company's system to try to get a feel for the system so that he or she can be more effictive at helping the rest of the group get inside during the real run. The computer security won't change between now and then, so they will face all th same protections.
Generally, give them plenty of information about the outside of the compound and what they can expect to find there, if they make some inquiries (bribes, hire someone to get the info, get it themselves, whatever). The inside (except the floorplan noted above), and especially Kisada's office should be a big mystery. No one seems to know anything about what's installed there. The men that installed the security system in Kisada's office haven't been seen around Night City since then...
CorpSec has been called in to provide a lot of additional security support for this office in the last month, because of the sensitivity of T112. Whik they have a lot of manpower and firepower behind them, the electronic security at YYY is minimal because they simple haven't ever been able to afford it (this deal was supposed to fix that). Aliow and help the players to be as creative as possible for gerting in and out of the Offices without getting into a fight with CorpSec. They just can't win a pitched battle with these guys.
The YYY computer system
The YYY computa system b not very well defended because their sensitive material is all located on the system that is inaccessible from the net, and they are still a struggling, young company. The system is INT 11, DEF 5. Use the basic layout and security of the sample Datafort (pa 163) with the following exceptions:
- 1: The FCT of all programs listed are
reduced by two.
2: Any reference to a human sysop i5 instead a FCT 4 Spy with a FCT 5 Fenris.
3: The "physical" description of the Datafort is as follows: The Datafort appears as a gothic cathedral (e.g. Notre Dame) with high arched ceilings. Alcoves and twisty staircaxs lead users off to the various subdirectories of the System. There is a giant stained-glass window of the YYY company logo on the north end of the main hall. The various rooms are all as bare of adomments as the main hall, but offer more comfort than the wooden pews. Conference rooms have large oak tables surrounded with padded chairs. Icons use the medieval motif as well (Ferris is a large mastiff, Blaster is a crossbow wielded by a squire, etc.).
The Compound
YYY's offices are right now just a lot more wellprotected than a company this small ought to be. The compound is located just east of Night City about 2 minutes by car outside the Map on page 198 in the rulebook.
The compound has a small security office, which is staffed 24 hours a day by at least two guards. The guards are well-paid, attentive, and professional. They monitor the security computer system and cameras diligently. In the event a guard needs a snack from the Vend-O-Matic, his partner will remain behind -- the office is always staffed.
There are two more guards walking patrol around the perimeter of the office compound at all times. Once every hour, one of these guards will enter the office and check the interior, even when there are employees present. All guards are equipped with heavy autopistots and light body armor (equivalent to BodyTest Full Impact Roadrasher). Consider them to be average CorpSec (pg 241). They also have a universal key card, letting them move freely through the interior of the building.
Around the neck of each guard tucked under their armor, is a personalized "station key." Guards on partrol must use the key at four stations (shown on the map) on their patrol route to indicate that they have been by. If a guard fails to key in within the alloted time, the office is alerted by the computer. The system is set up so that each guard on patrol has to "key in" every 20 minutes, and hit the stations in the proper order. There is an armored Personnel Carier with a CorpSec logo parked just outside the security office. It has a turreted machine cannon. Ouch.
Kisada's computer syslem is an island in the net -- you can't hack into it from the outside. The only way to access the information the players need is from the office itself; either inside computer room of the offices, from Kisada's desk, or (if they're clever enough) by tapping into the fiberoptic LAN connection on the roof (electronics, Kitbash, Hayduking or Commo roll of 10). Luckily for the players, there are no cameras watching the roof.
The compound is surrounded by a 3m tall brick wall, which is covered in clinging vines. The vines, while decorative, also serve to hide the alarm system's sensor mesh. Should anyone so much as lean on the wall, the company's security system will pinpoint their location aml bring it to the security office's attention. The security office will monitor that spot closely to see if any mischief is afoot. Anyone unwise enough to climb the wall without defeating the sensor mesh will undoubtably be met on the other side by a pair of guards, as they are always in radio contact with the office and each other.
Fortunately for the players, the sensor mesh is not top-of-the-line anymore. It can be defeated in ten minutes with a Tech roll of 15 (Hayduking or Suburban Ninja of 10), provided that the character performing the task has tools and wire on hand. This will render a 3m section of mesh inoperative and safe to cross.
The compound is also protected by multispectral video cameras which are perched on the top of the main building. There are six cameras; their location and field of view is indicated on the map. The cameras feed video straight to the security office, and are equipped with passive infared imaging as well as visible light capability. The bottom line is that they can easily see the heat from an intruder's body even in utter darkness. They can even see the residual heat left behind by footprints for several minutes. The cameras pan quickly back and forth; it will be impossible to sneak by them as long as they are operational. It is possible to shoot them out, but that will of course raise the alarms.
A netrunning character (or Rache, if absolutely necessary) could "speed" the system aml substitute a video loop for the live feed. See the Computer System for YYY, below. Once the ard has located the right subsystem, it'll take an Information Systems roll of at least 21 (or Suburban ninja at 15) to get the loop in place. Even then, it will only go unnoticed by the guard at the monitors for 2d10+5 minutes.
A final option is to white out the cameras by introducing a strong heat source, like a thermite charge, into their field of view. This is effective but would draw a lot of attention. It's got to be really hot to white out the cameras -- a Molotov cocktail wouldn't do it. Again, Hayduking players could cause major problems in the camera systems, the more creative the better.
The interior of the compound has cameras in the hallways and in the high-security labs. These cameras operate just like the ones outdoors, and can be defeated the same ways. A player will have an additional +1 difficulty for each camera that is being worked around.
While they are inside, the players will have to avoid or incapacitate the guards, but should avoid armed conflict. The guards are much more heavily armed and have nearly infinite backup; YYY has an Emergency Contract with CorpSec to provide 50 armed security in under 10 minutes if the situation warrants, and any firefight inside the compound ground will trigger this response. However, as you will see in Part Two, this may be to the players' advantage, since the CorpSec team that arrives will be loyal to Arasaka. Any Scanners in the group should be able to track the guards' movements and keep the players one step ahead of the guards.
 If the players take out a guard, they can use
his key card to get around inside, but this could
alert the guard at the security office due to the
unusual movement pattem. If the players move
around without a key card, they will need to
defeat each electronic lock through a "friend"
inside the computer systems (see the Datafort
diagram), with electronics work at each door (Use
Thief Stuff or Suburban Ninja: 2 minutes at a
difficulty 10 for most, 5 minutes and diff = 20 for
high security areas), or by brute force (the doors
and walls have SDP = 15, and will certainly set off
the alarms if blown through).
If the players take out a guard, they can use
his key card to get around inside, but this could
alert the guard at the security office due to the
unusual movement pattem. If the players move
around without a key card, they will need to
defeat each electronic lock through a "friend"
inside the computer systems (see the Datafort
diagram), with electronics work at each door (Use
Thief Stuff or Suburban Ninja: 2 minutes at a
difficulty 10 for most, 5 minutes and diff = 20 for
high security areas), or by brute force (the doors
and walls have SDP = 15, and will certainly set off
the alarms if blown through).
If the guards are alerted to the presence of the PCs, one patrol guard and one of the office guards will come to investigate. They have been ordered to restrain intruders if possible but to shoot to kill if necessary, and will perform their duties with enthusiasm. if in the evaluation of the guard in the security office they need reinforcements (armed resistance, or a team of greater than five people), then he'll call in CorpSec.
The security office itself looks like the little bunkers that gas station attendants work in. It's in the heart of the building, and has a physical lock on the door; wizards and electronics won't help. You canuse brute force, a lockpick, or a dextrous tinman could use tendrils to open the lock at a difficulty of 20, or an alchemist could realign the tumblers to "open" at a difficulty of 20. However, the guard on the inside has a weapons cache and body armor available. If he doesn't want to come out, he's nigh invulnerable.
Kisala's office likewise has a different security system from the rest of the lab -- a retina scan and number code are needed to get past Kisada's door. If a netrunner is present, the Retina scan can be overcome, but for some reason the numberpad can't be touched from the computer system. The truth is, the numberpad is on the "fritz"; Kisada has put in requests to have it fixed for about 3 weeks, but YYY's repair team has been dragging it's heels. Kisada has been doing all of his work out of the computer room and lab which is where the backup of the test reports can be found.
ArcoRunners could track out the tunnel system that runs undemeath the YW office; this will lead to a janitorial closet inside offices. The group should also try to negotiate with the local Trogs (from the Bastile Day supplement) -- they've got all of the alarms in those tunnels shut down, but would be unhappy if someone were to walk around down there without "askin' real nice."
It is possible to create a diversion which will draw the CorpSec to one end of the compound and then direct the "assault" on the other. Use your judgement on what would draw the CorpSec's attention, but keep in mind that they are very suspicious right now (they have been told that possible terrorist activity is possible) and will tend to check out just about anything unusual.
The Roof
If the players get a schematic of the computer systems at YYY, they will get a tech (Hayduking, Kitbash, Commo, or Schoolin') roll at a 10 to notice that the LAN of the internal system has a connection on the roof. Players who reach the roof will notice immediately that all of the sensors and other security hardware point away from the building, and that they can work in relative peace unless the alarm has already been raised. In the center of the roof is the fiberoptic line that connects with the internal computer system. It will require one of the following to connect a player's V-Term to the line (a Data Tap or, Commo 10, Hayduking 20, Electronics 10, Tech 15, Schoolin' 20, Kitbash 15). If they make the connection, the results in the "Main Computer Room" section happen to them on the roof.
Kisada's Office
If the players actually get in here, they shouldn't have too hard a time telling that it hasn't been used in a while. It reeks. Kisada left the remains of his lunch in the wastebasket when he was last able to get in the office, and by now the mildew smell is overpowering. There's really nothing in here -- all the data they need is in the main computer room, where Kisada has been working.
The Main Computer Room
There are two mainframes in this large, refrigerated room. As they enter, the larger of the two is across from the players, but the one they want is to their right (east end of the room). The primary mainframe has a single terminal and makes up the core system represented by the datafort.
Kisada's computer is what the players care about: it has a nice little display show, ing the message "Welcome Dr. Kisada.. There is a convenient little slot beneath the display for Rache's smartcard. If someone decides to hack into the system (eveything they need is right in front of them, and security is a joke for this system -- the guards are supposed to keep everyone from ever touching it), they can easily glance across all of the experimental results. Honestly, though, who cares? It's mostly going to mean nothing to these kids.
As soon as they jack the smartcard in, there will be about 10 seconds of strange flashing lights from the display before the Wrath of Rache destroys the system. If a wizard is inside of Kisada's system during this, it should be a mind-blowing experience; give him or her a REF roll at a 15 to get out of the system in time not to be mind-wiped along with the computer system. Rache's smartcard pops out of the console with all the data.
When Kisada's system comes crashing to the ground, its dying effort is to flip an alert switch in the security office. Regardless of how careful they have been up to now, CorpSec knows they're here, and things are about to get sticky. The players hear the voice of one of the CorpSec agents coming over the loudspeaker:
"Dr. Kisada? Is that you? Dr. Kisada? Something's wrong with your system, Doctor. I'm sending some of my men over." This is the best place to end a session.
Bring the kids back for next issue as they try to get the pretty card back to the Rock & Taco.
How to Use Jack Outside of Cybergeneration
"...And Jack Left Town" may be used in any of the Cyberpunk RPGs Cyberpunk, GURPS Cyberpunk and Shadowrun) the market with a little extra work. Keep in mind that players of other systems may not have as such practice at working around problems as CyberGen players (instead being used to relying on superior firepower). You may need to make the superior firepower of the security very obvious and increase it if necessary).
The T112 program is going to have to change a bit; it could, for instance, be a brand new nasty trackng program that will track a hacker back to his deck in half the time of current racers. The Players will hired by an semi-mythical figure to do the run. Use an appropriate dollar figure to get the players interested (unlikely cybergenerartion, these other systems rarely have altruism as a motivator).
For Shadowrun, you will need to add some magical flavor including a mage security guard. Have several of the CorpSec be Orcs Trolls and Dwarves. Instead of software, T112 could be a biological virus that attacks and kills a certain type of Metahuman (all Orcs, for example).
Back to Shadis #25 Table of Contents
Back to Shadis List of Issues
Back to MagWeb Master List of Magazines
© Copyright 1996 by Alderac Entertainment Group
This article appears in MagWeb (Magazine Web) on the Internet World Wide Web.
Other military history articles and gaming articles are available at http://www.magweb.com