Note: Game components not available on MagWeb.com--RL
 I. Introduction, Welcome to Cyberspace
I. Introduction, Welcome to Cyberspace
In the early 21st century, a global computer network called the Net is openly used by the STATQUO (government, corporations, organized crime, "the system") to maintain global domination. STATQUO's power is challenged by computer hackers called Cybernauts. The game revolves around the struggle between Cybernauts and STATQUO for control of the Net. One side, called the Netrunner, represents a group of active Cybernauts. The other side is the NSA, STATQUO's Net Security Agency. The object of the game is for the Netrunner to destroy or take control of as many electronic files on the Net as possible. The NSA uses its computer resources and agents to preserve the Net's integrity by blocking Netrunner activities and by discovering the whereabouts of Cybernauts and eliminating them through execution.
II. Basic Concepts and the Components
A. The Map
1. The left side of the 11 x 17 inch playing area contains a global map called RealWorld. The black zones in RealWorld represent vast built-up urban areas called Sprawls. Each Sprawl has a name and a special symbol indicating its Environ:
- Anarchy (breakdown of law and order)
- Corporatist (business and finance)
- Security (military and intelligence)
- Tech (electronic products and services)
Red-colored TransLines connect the Sprawls. The white circle with a number on each TransLine represents the cost paid for moving between two Sprawls.
2. The Cyberspace Display appears on the right half of the playing area. It is composed of four checkerboard grids that represent the world computer Net. Each square space with a red-colored border is called an address. There are three smaller nine-address Core displays (marked A, B, and C) and one larger 100-address grid labeled Central Matrix. Green-colored addresses containing the name of a RealWorld Sprawl are access points that permit one Cybernaut beginning a Netrun to enter Cyberspace at the node (computer connection) from the corresponding Sprawl in RealWorld.
A Cybernaut may begin a Netrun in a red-colored GAP (General Access Point) from any Sprawl location in RealWorld. The only other way to enter Cyberspace is at an address containing a Nexus or Back Door Cyberchit (see the Chit Explanation chart).
3. The Cybernauts Display beneath RealWorld contains ten boxes that hold all files and equipment carried by individual Cybernauts.
4. The red-colored Eliminated Cybernauts box holds all Cybernauts killed in the RealWorld or Cyberspace. They remain there and count toward the NSA victory point total unless returned to play by a "BodyBank" result during an Interaction attempt. (See Interaction Table.)
5. The blue-colored Destroyed NSA Files box is where NSA Files eliminated from play during a CyberStrike (VII.G.) are kept so that they can be counted in the Netrunner's favor at the end of the game.
6. The Destroyed NSA Cyberchits box is where all eliminated NSA Cyberchits other than Files are placed.
7. The Record Track beneath the RealWorld map contains spaces numbered 0 through 10. Use the Turn, Impulse, and Ops Points markers to indicate the game turn, Netrun impulse, and the current number of Operations Points available to a side during a Netrun impulse. Use the SS Max marker to record the maximum number of NSA Security Service units that can attack and move during an NSA turn whe never the Netrunner has destroyed or currently controls the COMSAT Cyberchit. (See the Chit Explanation chart for details.)
B. The Playing Pieces
The cardboard counters represent individual Cybernauts, NSA forces, Cyberchits, TechGear equipment, and various markers. The number of counters provided in the game is a deliberate limit. If all are in play, no additional ones can be received for any reason.
1. RealWorld units represent individual Cybernauts or NSA Security Service (SS) teams. These units operate only on the RealWorld display
2. Cyberchits represent various computer programs, system files, and special software. Each side has its own set of Cyberchits. A full description of each type can be found in the Chit Explanation chart.
3. TechGear chits represent RealWorld hardware that can enhance the physical abilities and survival of Cybernauts. A full description of the TechGear chits can be found on the TechGear Explanation Chart.
C. Charts and Tables
Several charts are used to execute game functions. These include a RealWorld Combat Results table, an Interaction table to determine the outcome of Netrunner attempts to gain resources, and the Unit Definitions to explain what kills what and what the names of all the Cyberchits and TechGear mean (along with any additional instructions on their use not covered in the rules).
D. Players must supply the following items:
III. Setting Up the Game
Set up the game according to the following instructions:
A. NSA Placement
The NSA player places all NSA Cyberchits provided in the game in Cyberspace.
1. A maximum of one Nexus and one File chit can occupy a single address. There is no limit to the number of other chits that can be placed in the same address.
2. No chits may be placed in a green- or red-colored address (i.e. a Sprawl name or a GAP).
3. Place at least one Nexus chit that is not marked "Dead End" in each of the Core grids (A, B, and C) and in Central Matrix, within the restrictions noted above.
4. Place each remaining Cyberchit anywhere in Cyberspace, within the restrictions noted in 1. and 2.
B. Cybernaut Setup
The Cybernaut side then sets up.
1. Choose from one to five Cybernauts. Place each on its hidden side (indicated by the icon picture) in any Sprawl on the RealWorld map except NORAD, L-5, and COSMOgrad. Any number can be placed in a single Sprawl.
2. Place all Netrunner Cyberchits and TechGear chits in one of the opaque containers.
3. Place all NSA SS units in the NSA container. The NSA player randomly chooses from the container a number of SS units equal to the number of Cybernauts the Netrunner chose. Place each SS unit in any RealWorld Sprawl. Any number of SS units can be placed in a single Sprawl.
IV. Playing the Game
A game lasts ten turns. During each turn, activities occur in the following order:
A. Netrunner Turn
1. Interaction: Conduct Interaction with any Cybernauts on the RealWorld.
2. RealWorld Movement: Move any Cybernauts on the RealWorld map (VI).
3. Netrun: Skip this segment, if desired, or conduct one Netrun in Cyberspace (VII).
- a. Set up the netrun
b. Impulse one
- 1. Netrunner conducts movement and cyberstrikes
2. NSA conducts movement and cyberstrikes
3. Move the impulse marker up one space on the record track.
c. Impulses two through ten are conducted in the same way as impulse one.
d. Logoff
B. NSA Turn
1. Attack: SS units may attack revealed Cybernaut units on the RealWorld map (VIII).
2. RealWorld Movement: Move any SS Squads on the RealWorld map (VI).
3. End of Game Turn: Advance the Turn marker one space. All Encounter effects end. At the end of the tenth turn, the game ends and the players determine victory.
V. Interaction
During Interaction, each Cybernaut may attempt to gain Cyberchits from the Sprawl it occupies. An Interaction attempt is entirely voluntary; but, if attempted, it may trigger a random event called an Encounter or cause the Cybernaut to become revealed (V.C.) and thus vulnerable to attack in the RealWorld.
A. Carrying Out an Interaction
Resolve each Interaction attempt on the Interaction table. Roll the die and add the result to the RealWorld value printed on the Cybernaut's counter (upper left). Cross-index the total with the Sprawl's Environ type and immediately apply the outcome.
B. Restrictions
1. No Cybernaut can be involved in more than one Interaction attempt per Netrunner Turn.
2. If a Sprawl contains two or more Cybernauts, they can each make separate Interaction attempts, combine to make a single attempt, or have some form groups and others act alone. The Netrunner side is free to decide exactly what approach it wishes to take for each Sprawl.
3. If more than one Cybernaut participates in an interaction attempt, use the highest single RealWorld value to resolve the attempt. Cybernauts may not add their RealWorld values together. (A group has a better chance of surviving Encounter results arising from Interaction.)
C. Hidden and Revealed Cybernauts
Hidden Cybernauts (indicated by the human figure on the counter) cannot be attacked by NSA units on the RealWorld map. Cybernauts that become revealed continue to function normally in all ways, but they are subject to attack during the Attack segment of an NSA turn. When a Cybernaut is revealed, flip it over to the side containing the target symbol.
1. Cybernauts are revealed when
- An A result occurs on the Interaction table
- A System Alert is triggered (VII.B.5.).
2. A revealed Cybernaut that receives another Revealed result suffers no further effects.
3. When a Cybernaut becomes revealed:
- The NSA receives reinforcements (V.E.2.).
- All chits in the revealed Cybernaut's holding box are flipped over so that they can be seen.
4. The NSA may examine Netrunner Cyberchits in a revealed Cybernaut's holding area. The holding boxes of hidden Cybernauts may not be examined.
5. A Cybernaut returns to Hidden status the instant it receives certain results on the Interaction table or stops in or passes through a Sprawl that has become an "Autonomous Zone." (See Chit Explanation chart for details.) Flip the newly hidden Cybernaut back over to the side containing the human figure. Also be sure to flip all chits in the Cybernaut's holding box so that their contents can no longer be seen by the NSA side.
D. Encounters
An E result on the Interaction table requires that the Encounter table be consulted. Roll the die twice: multiply the first die roll by ten and add the second die roll to it. Find the total on the Encounter table and immediately apply the effects. Perform Encounter Combat if necessary. Players should note which Sprawl the Encounter affects for the remainder of the game turn.
E. Receiving New Units
1. The Netrunner side may receive more Cybernauts, due to a "Recruit" or "BodybanW' Encounter result, up to and limited by the countermix. Netrunner reinforcements are placed in the Sprawl where the Interaction attempt was made.
2. The NSA receives one SS unit each time a hidden Cybernaut is revealed for any reason. The NSA picks the unit at random from the NSA container (if any units are available) and places it in any RealWorld Sprawl.
VI. RealWorld Movement
Cybernauts and SS units move from Sprawl to Sprawl on the RealWorld map via TransLines during a friendly RealWorld Movement segment. NSA units may not move during the Netrunner turn, and Cybernauts may not move during the NSA turn. Each unit has a movement ability equal to its RealWorld value (upper left). A unit must end its movement in a Sprawl, not on a TransLine. Possession of particular TechGear chits will enhance a Cybernaut's movement capability.
A. Procedure
1. Each time a unit moves via a TransLine it must expend a number of points from its total RealWorld equal to the TransLine's printed value.
2. Each point can be used only once during the segment.
3. If a unit does not have enough unused points left to enter any Sprawl connected to its current location by a TransLine, the unit must cease moving for the current segment.
4. A unit may choose to stop in a Sprawl and move no farther, even if it has unused points remaining. Unused points may not be saved for later use or transferred to another unit.
B. Moving in Groups
More than one unit may move together at the same time. 1. Use the single highest printed RealWorld value in the group to determine how far the group can travel. 2. A group of units moving together must stay together for their entire movement. No units in the group may be dropped off and none can be picked up along the way. 3. Units may freely enter, leave, and move through Sprawls containing enemy units without extra cost or penalty.
C. Carrying Chits
Cybernauts can carry Netrunner Cyberchits, TechGear chits, and NSA Cyberchits controlled (that is, captured via cyberstrike) during Netruns. Place Cyberchits being carried by a Cybernaut in that Cybernaut' s holding box on the map.
1. There is no limit to the number of chits a Cybernaut can carry.
2. Any number of chits may be transferred from one Cybernaut to another during Netrunner RealWorld Movement, as long as the Cybernauts occupy the same RealWorld Sprawl at the instant of the transfer. A Cybernaut or group of Cybernauts may temporarily interrupt movement to perform a transfer. There is no limit to the number of transfers a Cybernaut can participate in during Netrunner Movement.
3. Carrying and transferring chits costs no movement points and does not reduce the carrying unit's Realworld value.
VII. Netruns
Only the Netrunner side may perform a Netrun. Only one Cybernaut may make a Netrun each Netrun segment. During the Netrun the Cybernaut is represented in Cyberspace by the Ghost marker. Netrunner and NSA Cyberchits can be moved (if they are capable of movement at all) in the Cyberspace grids and conduct CyberStrikes (electronic combat) during a Netrun. No movement or combat occurs on the RealWorld map during a Netrun segment.
A. Setting up the Netrun
1. The Netrunner designates one Cybernaut.
2. The Netrunner places the Ghost marker in one of the following locations in Cyberspace:
B. Netrun Operations
Each Netrun consists of no more than ten impulses. The following occurs in each impulse:
1. The Cybernaut selected by the Netrunner may conduct a number of operations in Cyberspace equal to its printed Wetware value (lower left corner). At the beginning of each Impulse, place the Ops Points marker in the numbered space on the Record Track corresponding to the Cybernaut's Wetware value.
2. After the Netrunner side completes whatever operations it wishes to perform, the NSA receives a number of operations points equal to the number of Control and face-up Ice Cyberchits currently in Cyberspace. Place the Ops Points marker in the proper numbered space on the Record Track.
3. Operations may be conducted in any order. There is no need to complete all movement before undertaking CyberStrikes. A Cyberchit or Ghost marker may freely mix movement and CyberStrike combat. For example, it could attack first, move, attack again, and so forth. Only the number of operations points available limits the amount of activity. Deduct points as they are used from the active side's current total. The cost for each type of movement or action is listed on Operations Chart.
4. Only Cyberchits in the holding box of the Cybernaut performing the Netrun can be placed in Cyberspace through the expenditure of operations points. No other Cyberchits are eligible. Netrunner Cyberchits are always placed face down in Cyberspace.
5. Each time the Ghost marker or a moving Netrunner Cyberchit enters an address containing face-down NSA Cyberchits, they are all flipped over. If one of the revealed chits is labeled Ice and it survives the CyberStrike that immediately follows, a System Alert occurs, which reveals the Cybernaut making the Netrun on the RealWorld display, if it is currently hidden.
6. The Netrunner side gains control of (that is, captures) any and all NSA Files the instant the Ghost marker enters the address the file chits occupy and he has a cyberchit capable of defeating it, which he must use to do so (see Cyberstrikes). Place controlled Files in the map holding box of the Cybernaut making the Netrun. For details about the special advantages various Files can provide, see the Chit Explanation chart.
D. Stacking
Stacking is having more than one Cyberchit on an individual address.
1. The NSA may have one Nexus, one File, and an unlimited number of other NSA Cyberchits in a single address at any time during an impulse.
2. The Netrunner may have any number of Netrunner Cyberchits in the same address.
3. Cyberchits from opposing sides may occupy the same address. Netrunner chits do not count toward NSA stacking limits.
E. Moving in Cyberspace
AH Cyberchits with a white circle (in the lower right corner) containing a green letter and the Netrunner Ghost marker may move in Cyberspace. All other Cyberchits (indicated by a red box with a white letter) must remain in the address in which they are placed throughout the Netrun until they become controlled by a Cybernaut making a Netrun or are eliminated.
1. Linear movement within the Central Matrix or within a single Core grid occurs from address to address. A Cyberchit may move across the side of an address, but never through the vertex (corner).
2. Nexus "jumps" between one address and another in the same grid or different grids can occur regardless of the distance between the two if both addresses contain matching Nexus chits. Nexus chits match if they both have at least one common number (1, 2, or 3) printed in red on their counters. A Nexus with no numbers and the label "Dead End" cannot be used to make jumps to any other location. (It represents a "dummy program" intended to prevent penetration of the Net.)
3. A Cyberchit or Ghost marker may move any number of times each impulse. Each red address boundary crossed using linear movement costs one operations point. Each Nexus jump costs one operations point, regardless of the distance travelled.
F. Revealing Cyberchits
The contents of an NSA or Netrunner Cyberchit remains hidden until one of the following happens:
1. A moving chit enters an address containing any enemy chits, or its address is entered by a moving enemy chit.
2. The chit moves adjacent to an enemy chit containing an eye symbol in the lower left corner (that is, an NSA Tracer or Netrunner Probe). The Tracer or Probe must first be revealed if it is currently hidden, followed by all enemy chits in all adjacent addresses.
3. A chit with an eye symbol is revealed by the owner. All enemy chits in all adjacent addresses are revealed. Addresses that share only a vertex (corner) but not a red border with the Tracer or Probe's address are not considered adjacent.
4. If the NSA player uses a Tracer to reveal Netrunner cyberchits, the cybernaut in the real world is revealed, even if in an autonomous zone. The NSA player must be the moving player in this instance. If the tracer is revealed by a Netrunner cyberchit or ghost marker first, that tracer can no longer reveal a cybernaut in the real world through the duration of that netrun.
G. CyberStrikes
A CyberStrike represents combat in Cyberspace. The Netrunner can destroy Cyberchits that it cannot control or chooses not to control. The NSA can destroy Netrunner Cyberchits and can even neutralize or eliminate the Cybernaut performing the Netrun. A CyberStrike must occur when Netrunner and NSA Cyberchits occupy the same address. All Cyberchits in the holding box of the Cybernaut performing the Netrun are considered to be in the address occupied by the Ghost marker.
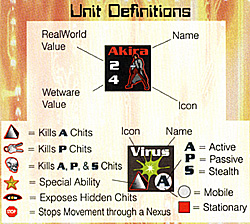
No die roll is needed to resolve a CyberStrike. The results listed under Unit Definitions are automatic and depend entirely upon the type of attacking and defending Cyberchits.
CyberStrikes cost no Operations points.
1. Procedure: Select one attacking Cyberchit and cross-index its CyberStrike symbol in the lower left corner to the class type printed in the lower right corner of every defending enemy Cyberchit. Check each enemy Cyberchit, one at a time, and apply all the results listed under Unit Definitions to the attacker and the defenders.
Continue the process until all attacking Cyberchits have had the chance to check Unit Definitions against all enemy Cyberchits in the same address.
The defender then repeats the process for all its Cyberchits at the address. Because CyberStrike combat is considered simultaneous, any of the opponent's Cyberchits eliminated during the CyberStrike have a chance to perform combat before being removed from play.
2. Cybernaut Neutralization and Elimination: Each NSA Cyberchit with a skull symbol has the potential to harm the Cybernaut if the Ghost marker is in the chit's address. Roll the die. The Cybernaut is neutralized if the result is the same or less than the Cybernaut's Wetware value. If the result is greater, the Cybernaut is eliminated.
If the Cybernaut is neutralized, immediately perform Logoff (VII. H.). In addition to normal Logoff procedures, all NSA File Cyberchits in the Cybernaut's holding box are returned to the NSA for placement back in Cyberspace during Logoff All Netrunner cyberchits currently in play in cyberspace are placed back into the Netrunner container.
If the Cybernaut is eliminated, perform neutralization and eliminate the Cybernaut from play. Place all the Netrunner Cyberchits and TechGear chits in the eliminated Cybernaut's holding box back in the Netrunner container. Place any controlled NSA files back in Cyberspace, as described in Logoff.
3. If at least one Netrunner Cyberchit or the Ghost marker survives a CyberStrike in an address containing a Nexus chit, every other Nexus chit containing at least one matching red number must be revealed along with any other NSA Cyberchits located in its address Exception: A Nexus chit occupying an address containing an Ice chit is not considered to be functioning, so no chits located in other addresses need to be flipped over.
4. Nexus chits cannot be eliminated by a CyberStrike.
H. Logoff
1. A Netrun ends after the conclusion of ten impulses. It may end sooner if either of the following occur:
- The Cybernaut is neutralized or eliminated during a CyberStrike.
- The Cybernaut announces Logoff immediately after moving the Ghost marker into an address containing any of the following:
- a. The name of the RealWorld Sprawl where the Cybernaut is physically located
b. The label "GAP"
c. A "Back Door" Cyberchit
Logoff costs no Operations Points.
2. If the Netrunner is still logged on at the end of the tenth impulse, the Cybernaut making the Netrun is automatically eliminated (VII.G,2). This rule represents a sort of electronic overdose.
3. When Logoff occurs, remove the Netrunner Ghost marker and set it aside. Place all Netrunner Cyberchits - except "Back Door" - in the Netrunner container.
4. Regeneration: After Logoff occurs, the NSA player returns to play from the "Destroyed NSA Cyberchits" box any one Cyberchit of its choice if any Control File is currently on the Cyberspace display (revealed or not). Destroyed Files can never be regenerated.
5. Once the NSA regenerates Cyberchits, it may move all of its Cyberchits and Files to new locations on the cyberspace display, including any Files retrieved from a neutralized or eliminated cybernaut. All chits are then flipped back over to their hidden side. All this is done in secret: the cybernaut player may need to leave the room. The only exception to this rule are Nexus Cyberchits: they may never be moved and once revealed remain revealed throughout the duration of the game.
VIII. RealWorld Combat
The NSA may perform RealWorld combat during the Attack segment of the NSA turn. The Netrunner side may fire back at that time, but cannot initiate RealWorld combat during its own turn. SS units in a Sprawl may attack any revealed Cybernaut units located there.
A. Procedure
1. The NSA announces an attack in a particular Sprawl and selects the SS units in the Sprawl that will participate.
2. The NSA totals the red-colored RealWorld values located in the lower left corner of all participating SS units. The Netrunner totals the RealWorld values printed in the upper left corner of all revealed (not hidden) Cybernauts.
3. First the NSA and then the Netrunner side resolves fire on the RealWorld Combat table. Because combat is considered simultaneous, Netrunner units fire back at full value even if eliminated by NSA fire.
B. Restrictions
1. The NSA may conduct only one attack in a Sprawl each NSA turn. Attacking is completely voluntary. Only NSA units specifically designated as part of the attack are affected by Netrunner return fire.
2. The Netrunner may never initiate an attack. (The NSA has so many agents that a conventional Cybernaut offensive would be futile and inevitably lead to defeat.)
3. Hidden Cybernauts are never affected by combat results and may never fire back.
C. Eliminated Units
1. Eliminated SS units are placed in the NSA container and are eligible to return to play each time a hidden Cybernaut is revealed.
2. Eliminated Cybernauts may never return to play, unless a "Body Bank" result on the Encounter table is received during an interaction attempt.
D. Encounter Combat
Certain Interaction results on the Encounter table call for the Cybernauts making the interaction attempt or SS units in the same Sprawl to conduct combat with various third parties (police, street gangs, and the like). This combat is performed the same as RealWorld combat, except that the Cybernauts or NSA units required to perform the Interaction fire first. If any result (I or E) is received, the combat ends. Otherwise, the opponent fires back with the value indicated in the Encounter instructions.
IX. NSA Movement
The NSA player conducts movement in the same manner as the cybernaut during this phase.
More Cybernaut The New Frontier
-
What is a Cybernaut, Anyway?
Some Cybernaut Technology
Some Cybernaut Organizations
Tools of the of Trade
The Zimmerman Case
Discovery of a New Frontier
Game Rules
Back to Table of Contents Competitive Edge #11
Back to Competitive Edge List of Issues
Back to Master Magazine List
© Copyright 1996 by One Small Step, Inc.
This article appears in MagWeb (Magazine Web) on the Internet World Wide Web.
Other military history articles and gaming articles are available at http://www.magweb.com